G DATA Mobile Device Management: Profile Administration
This article describes the profile management in G DATA Mobile Device Management
Profiles are similar to a group management. This means that different profiles with different settings can be created and then assigned to a device. Instead of creating groups of devices with the designations "Administration" "Sales" and "Technician", for example, profiles are created with the corresponding designations and given to the device during installation. Of course, profiles can be changed at any time. When the profile is changed, all devices with the corresponding profile will receive the changes the next time they have established connection to G DATA Mobile Device Management.
The settings recommended by G DATA are already combined in the "Standard" profile.
Profile creation and management can be found in G DATA Administrator → object tree Mobile Device Management → Profiles.
General settings of a profile
| Area | Description | ||
|---|---|---|---|
Virus scan |
|
||
Synchronization |
At what interval should devices with this profile send information about their status, installed apps and settings to G DATA Mobile Device Management? (every 6 hours, 12 hours, daily, every 2 days or weekly?) This setting can be made separately for WLAN connections and mobile data connections. |
||
SIM card protection |
If the SIM card is removed without permission, the device is locked with the lock screen and an acoustic alarm sounds. |
||
Guidelines for rooting |
With the Yes setting, you allow phones to be rooted. With No, rooted devices are reported to you as a security risk.
|
||
Updates to virus signatures |
Set how often the device should load virus signatures (daily, every 3 days, weekly, every 2 weeks or monthly). You can specify that updates should only be performed when there is a WLAN connection. |
||
Web protection |
You can specify whether you want to turn on web protection always or only for active Wi-Fi connections. The web protection supports Chrome, Firefox, Edge and Opera browsers for Android. |
||
WLAN Configuration |
Here you can store the data of your secured company WLAN if you want your users to use it as soon as they are within range of your company. The users do not need to know the credentials to be able to connect. |
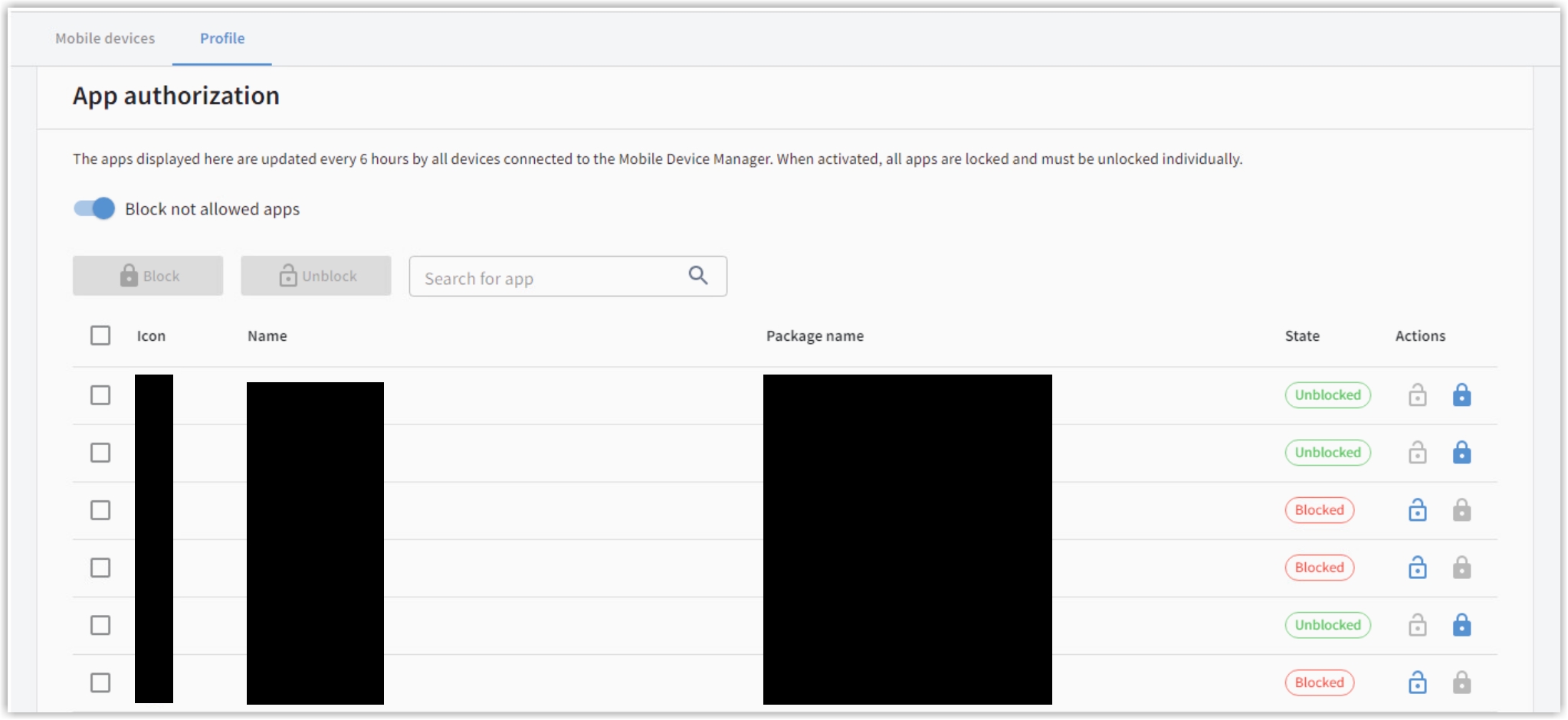
The app filter
In the Standard profile, all apps are allowed. In your self-created profiles, you have the option to specify whether you want to prohibit certain apps or allow only certain apps.
Use the "Block not allowed apps" slider to turn this feature on or off.
You will see a list of all apps that your users have on their devices. By checking the boxes and following the instructions, you can determine which apps are allowed and which are not. If you want to mark all apps or unmark all apps, check or uncheck the checkbox in the header.
Notifications
To avoid having to check the devices in the console every day, you can store one or more e-mail addresses here. We will send you a mail to these addresses as soon as a recommended action arises. This way you are always informed promptly. You can also select the language in which you would like to receive the mail.
The mailing is done from the e-mail address noreply@gdata.de.
If required, put the email address on your whitelist. This will prevent the email from being accidentally moved to your spam folder.
Since the notifications can be created via profiles, it is possible to specify different recipients and languages for different device groups.
Configure devices independently of profiles
When installing G DATA Endpoint Security Android or G DATA Endpoint Security iOS on a mobile device, it is mandatory to assign a profile. If a device is to be administered separately, it is possible to switch off the profile in the device configuration (in G DATA Administrator, select Mobile Device Management in the object tree and click menu item Mobile devices. In the device list choose the desired device. Then select Settings and turn off Use profile in the device settings).