G DATA 365 | Mail Protection
Protocols of the G DATA 365 | Mail Protection
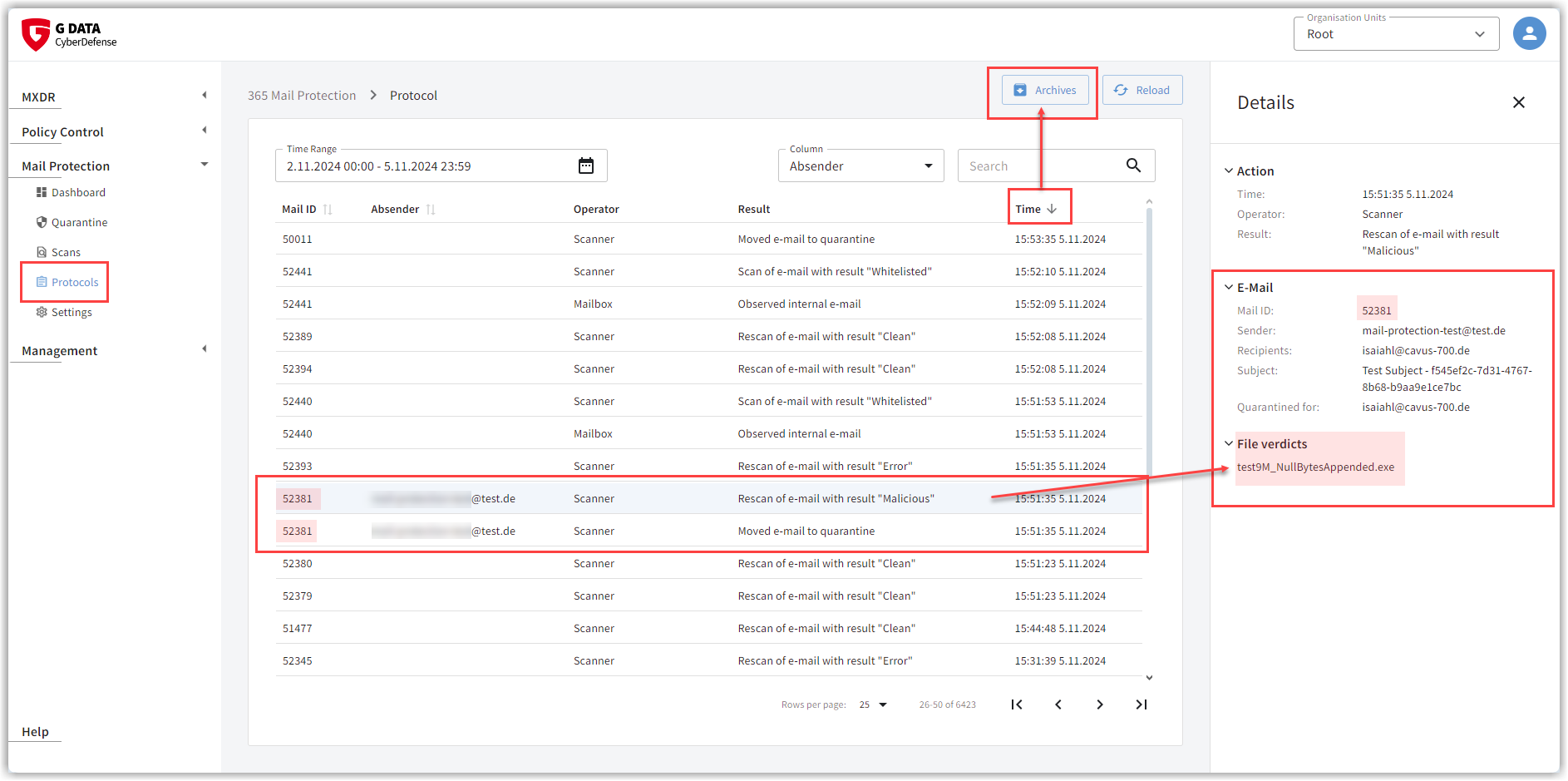
These actions of the G DATA 365 | Mail Protection are logged:
-
Incoming e-mails and their classification.
Each incoming mail receives a sequential number. In the log, you will be able to see by the number whether the e-mail has been forwarded to the recipient’s mailbox, moved to the recipient’s junk folder as spam or moved to quarantine as an infected email (see screenshot). -
Scan.
Every e-mail that has been forwarded to the recipient’s mailbox is checked in the mailbox at irregular intervals for a few days (rescan). In the logs you will find all Rescans, as well as scans that were initiated manually by a user. -
Change of settings.
Every change to the settings by users is logged.
By clicking on a line, you will receive further information about the affected e-mail and (in the lines created by the scanner) which detection has taken place.
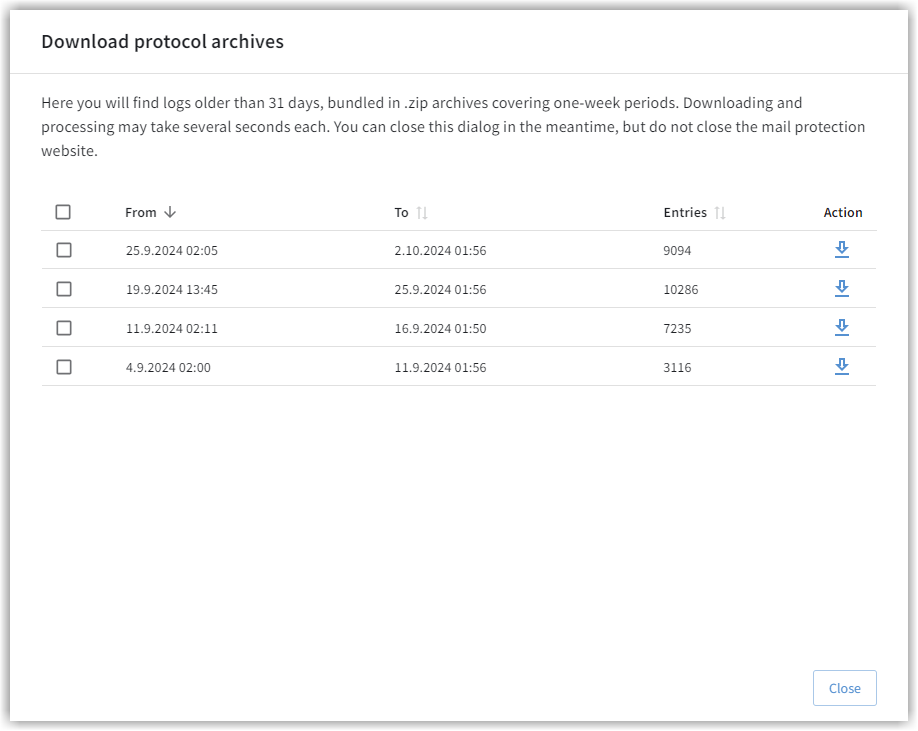
The entries are retained for 30 days. After that, they are bundled on a weekly basis and stored in *.zip archives.
If required, you can download the desired log periods via the Archive button.
| It may happen that an e-mail that has been moved to the junk folder, appears several times in the log due to a rescan. |
The columns can be sorted in ascending or descending order using an arrow next to the column name.