G DATA Phishing Simulation
Bypass Advanced Threat Protection in Defender P1 for links and attachments.
To ensure that the links and attachments of our simulated phishing e-mails are not deleted, the Advanced Threat Protection in Defender P1 must be bypassed.
Proceed as follows:
1. |
Open the Microsoft 365 admin center. |
||
2. |
Click on Security in the left side menu. Show screenshot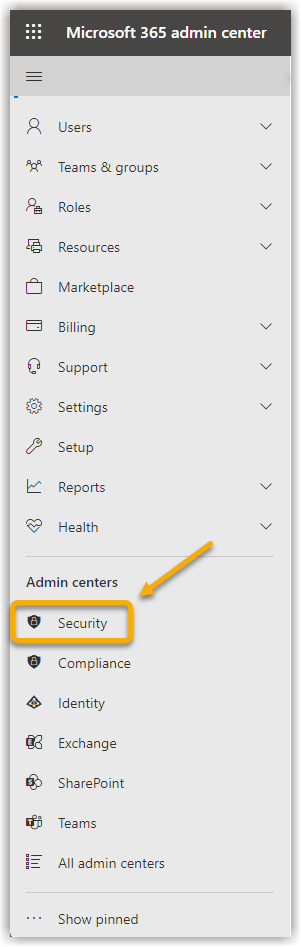
|
||
3. |
Click on Exchange Message Tracking in the left side menu. This will take you to the Exchange Admin Center. Show screenshot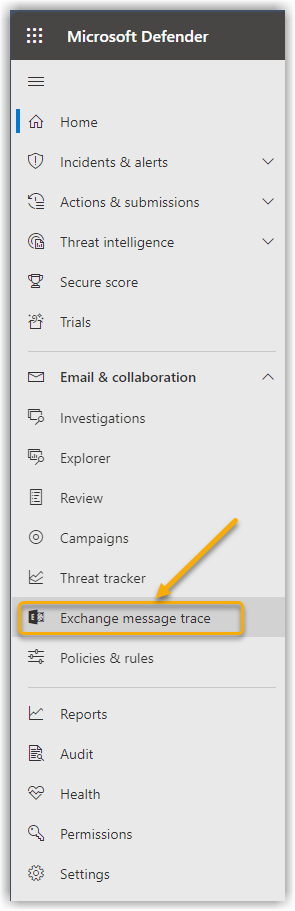
|
||
4. |
Click on Email flow in the left side menu and then on Rules in the submenu that opens. Show screenshot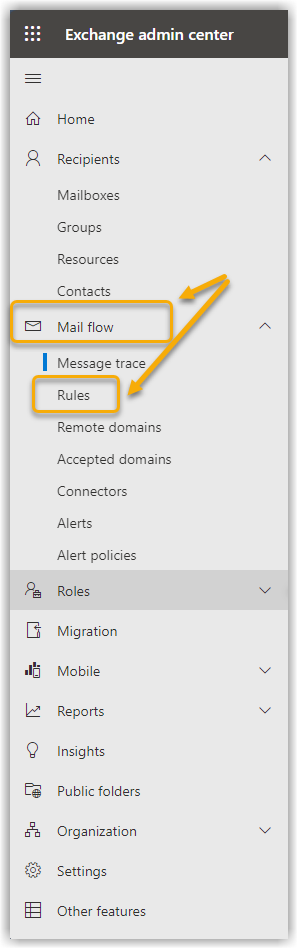
|
||
5. |
Click on Add a rule. In the submenu that opens, select Create a new rule. Show screenshot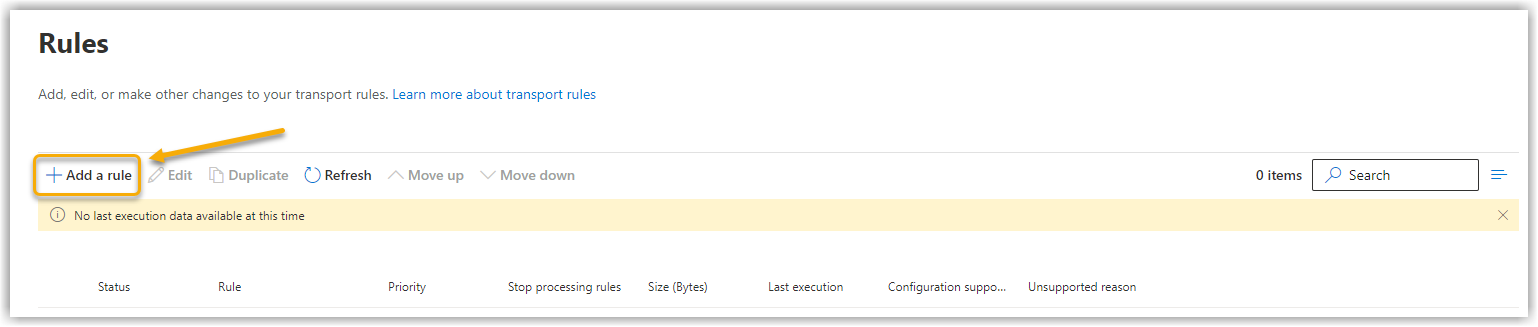
|
||
6. |
For Apply this rule if… select The sender in combination with IP is in any of these ranges or exactly matches. Show screenshot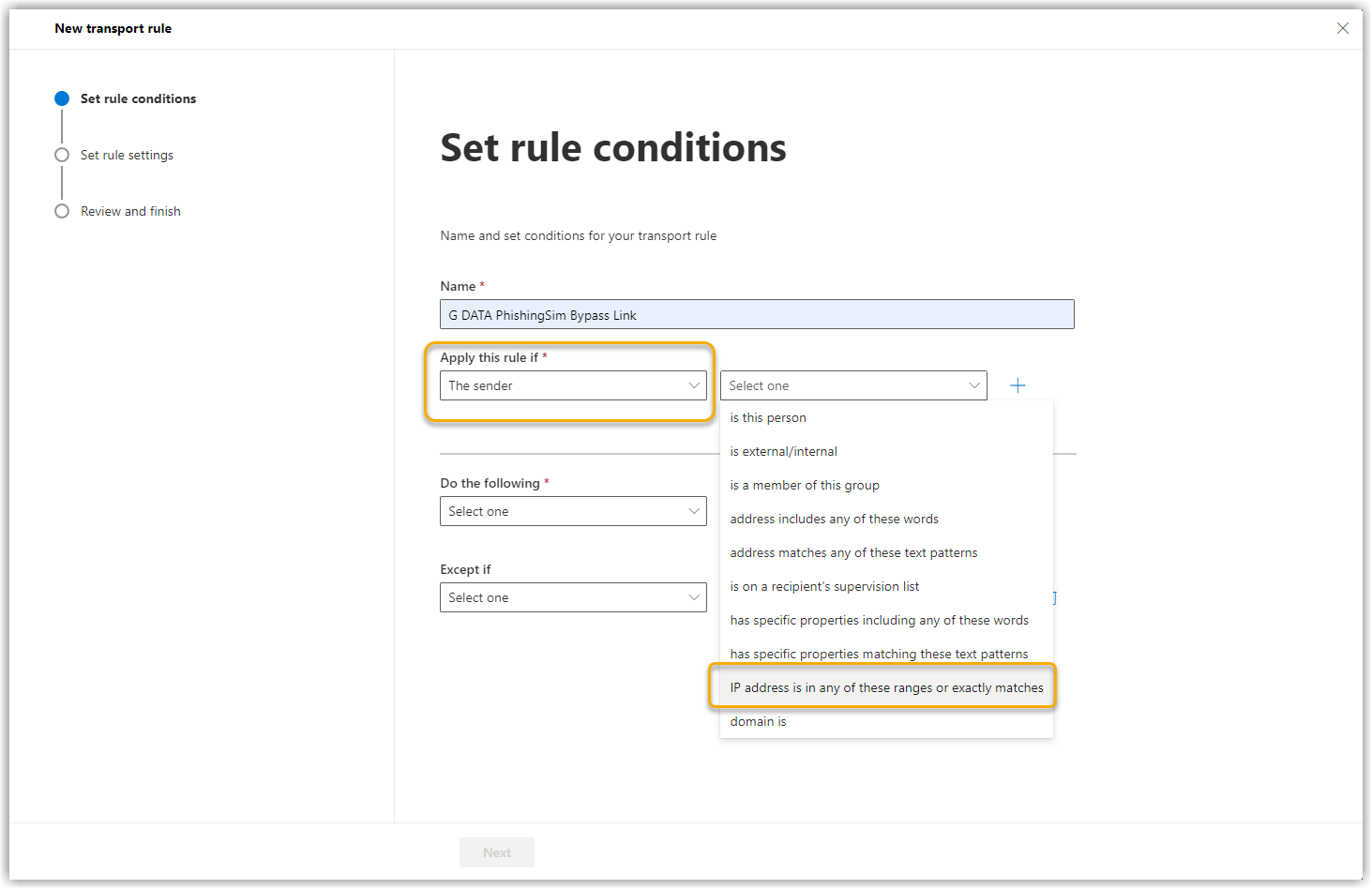
|
||
7. |
Now enter our IPs here.
Show screenshot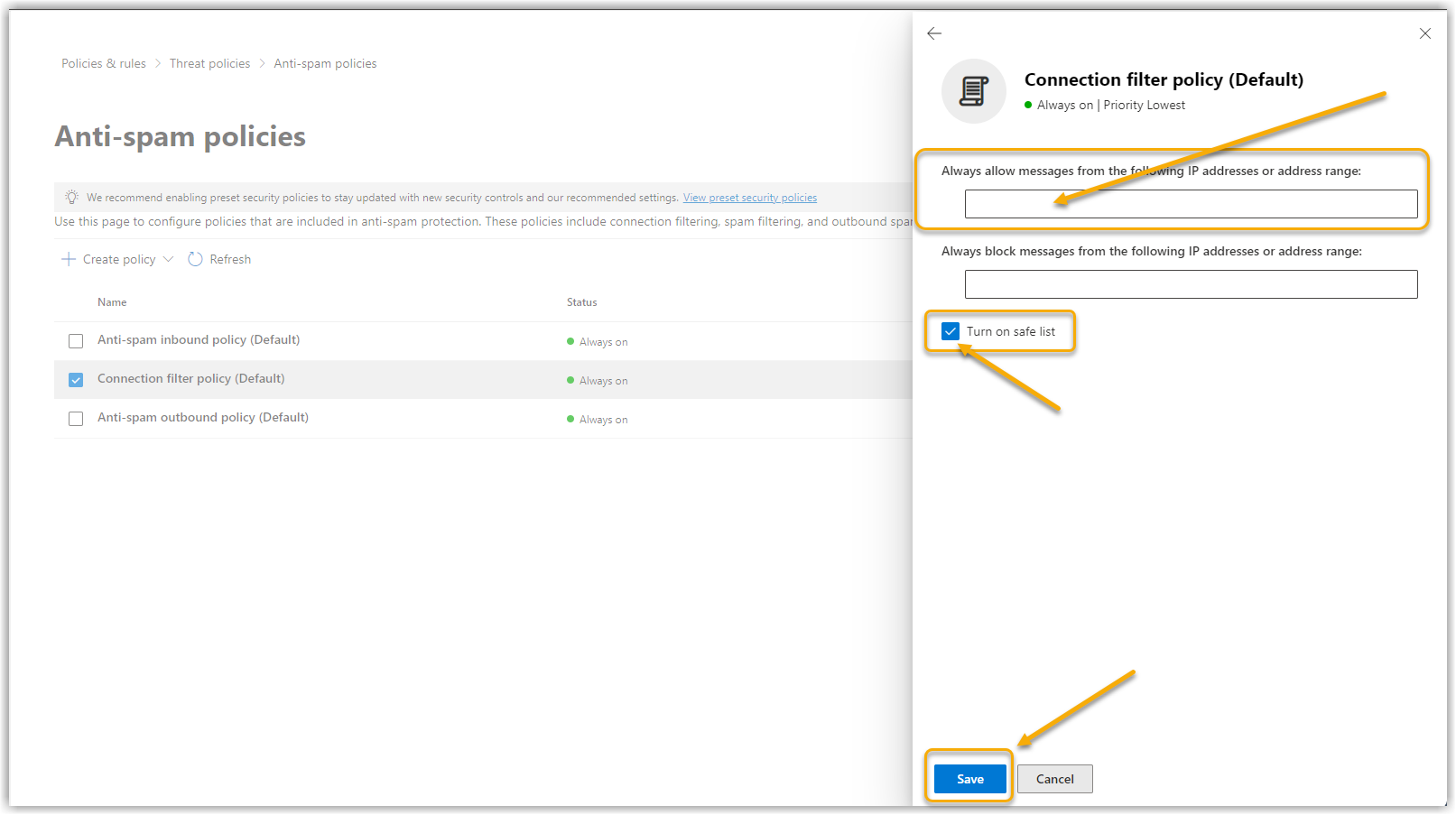
|
||
8. |
For Proceed as follows: select Define message header Show screenshot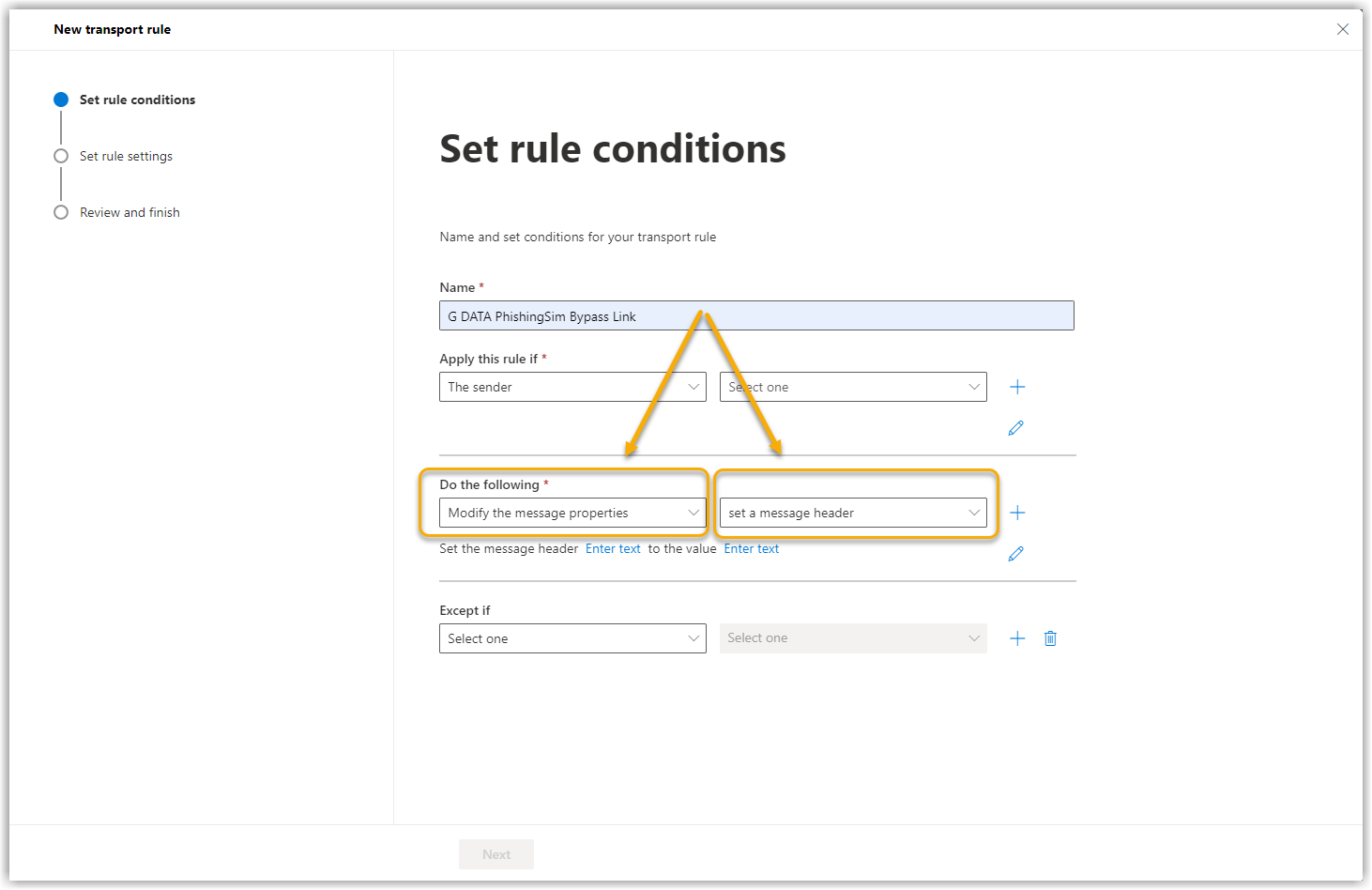
|
||
9. |
Click on Enter text. Click on Save. Show screenshot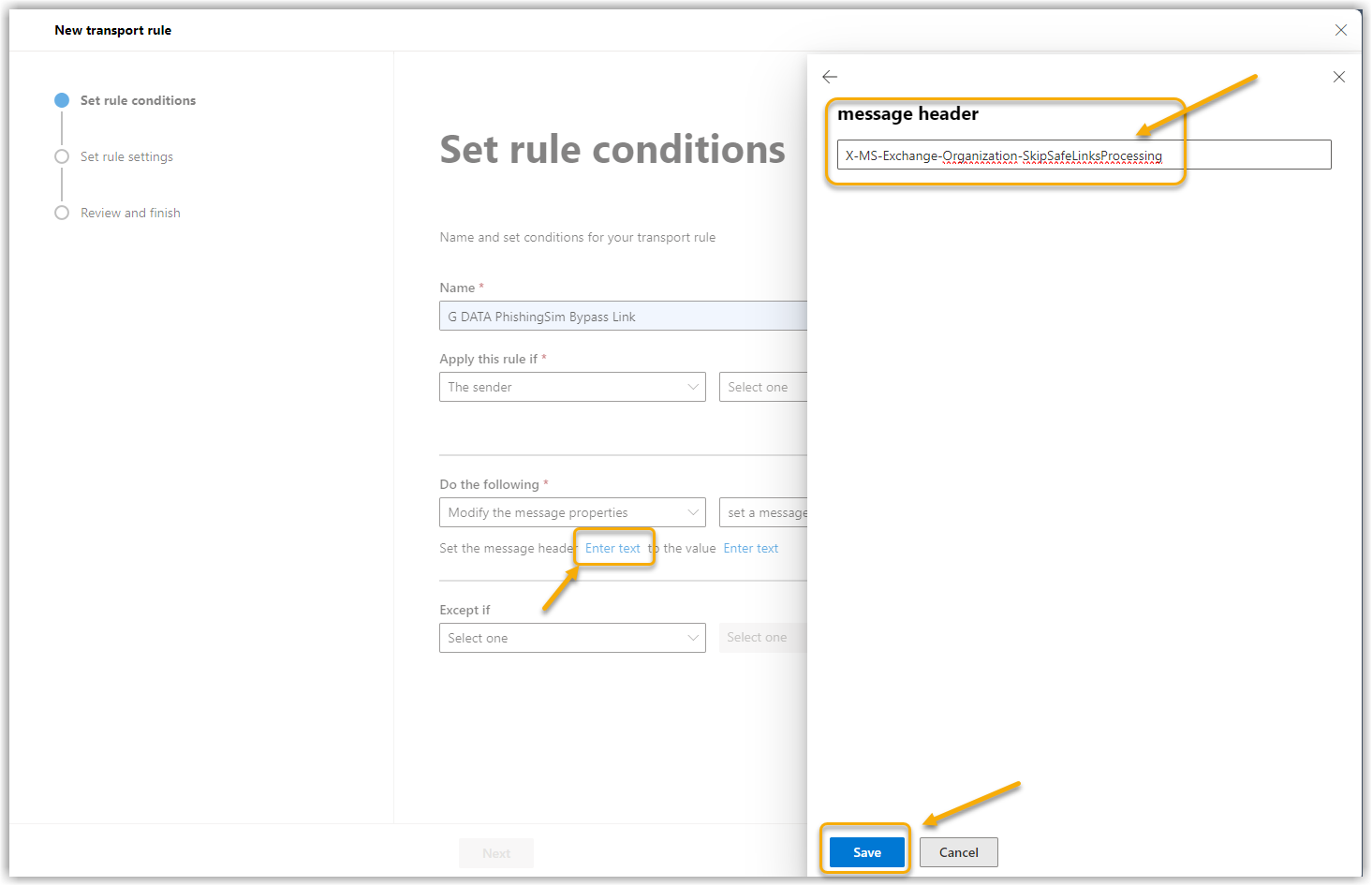
|
||
10. |
Click on Enter text. Click on Save. Show screenshot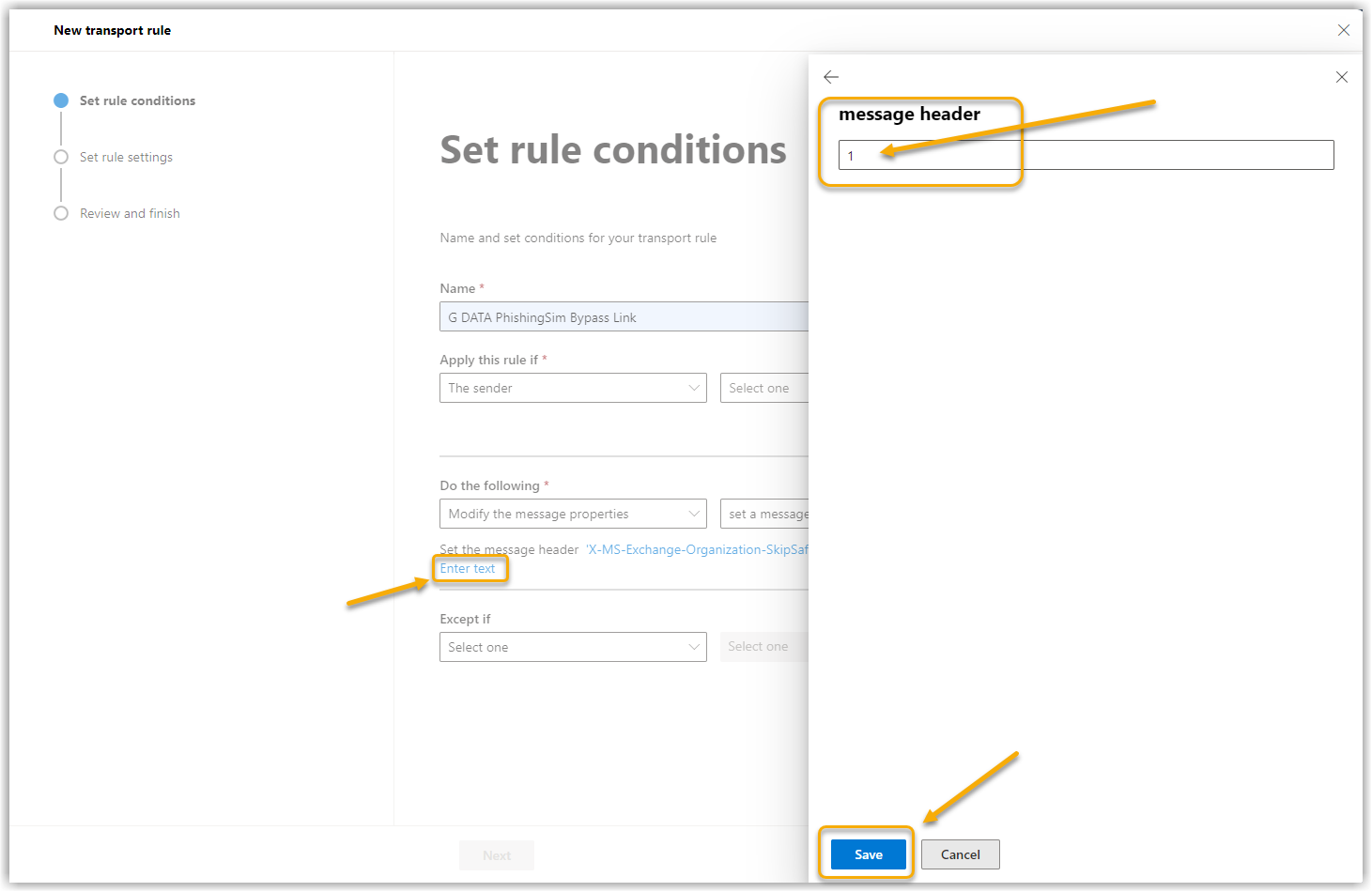
|
||
11. |
In the next window, make sure that the Rule mode is set to "Enforce" and select a severity level for this rule. Rule matches are grouped by severity in activity reports. The severity level is only a filter to ease the use of the reports. The severity level has no effect on the priority in which the rule is processed.
Show screenshot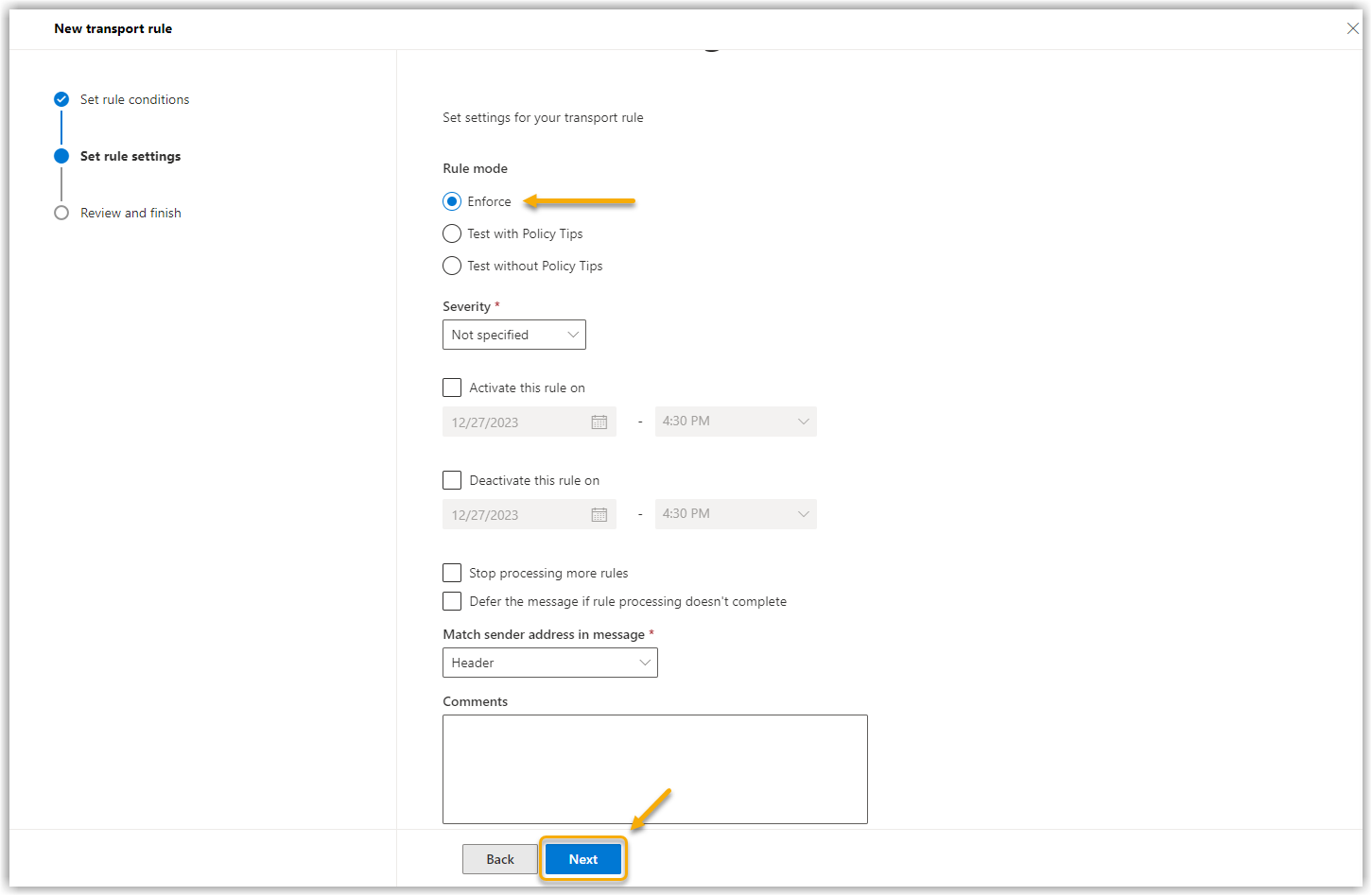
|
||
12. |
Click on Next. Show screenshot
|
||
13. |
Check the settings again in the next window and click on Finish. Show screenshot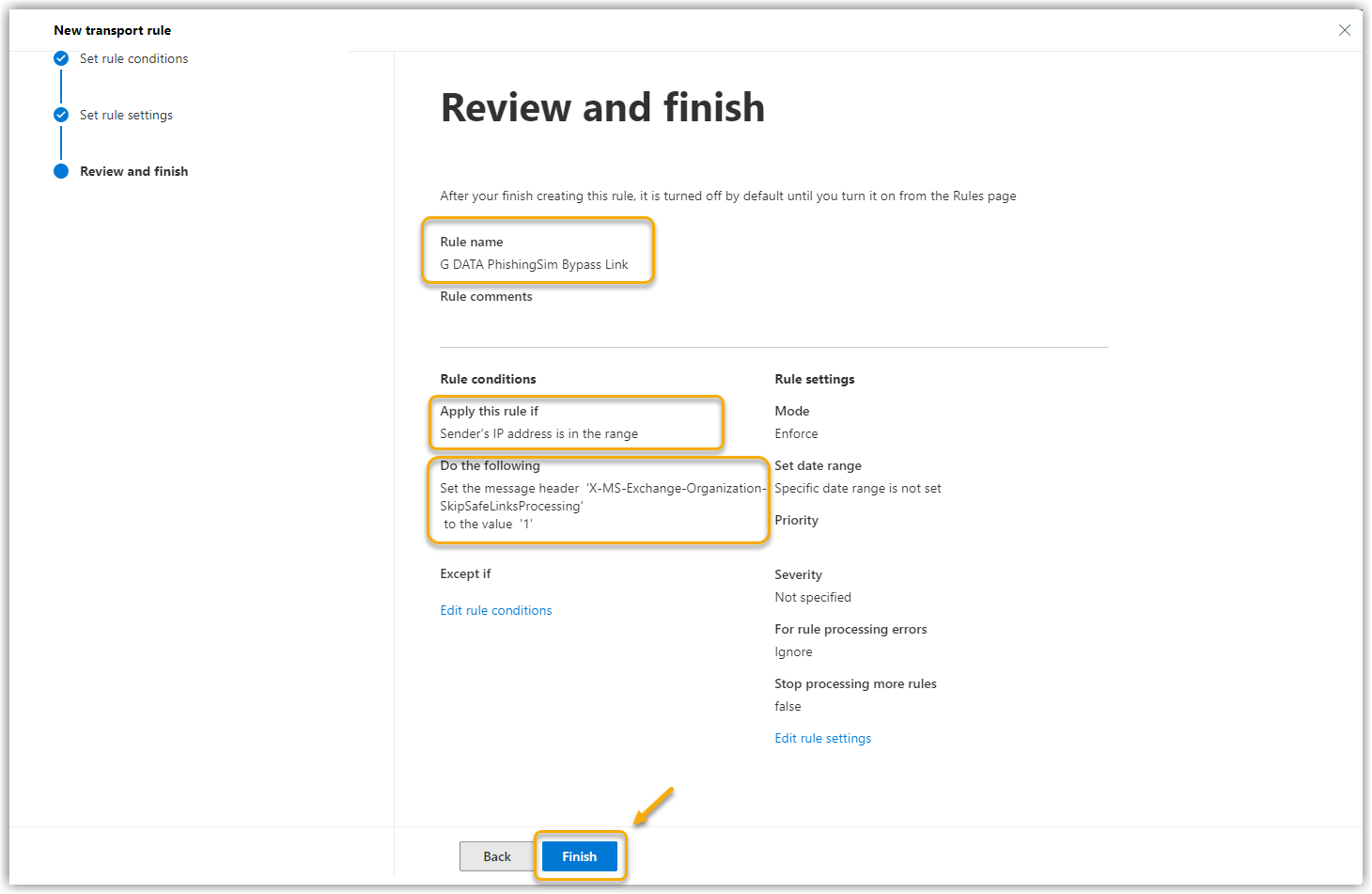
|
||
14. |
Your rule will then be available in your rule overview. However, it is still disabled. Click on the word Disabled and a new window will open on the right-hand side of the screen. Show screenshot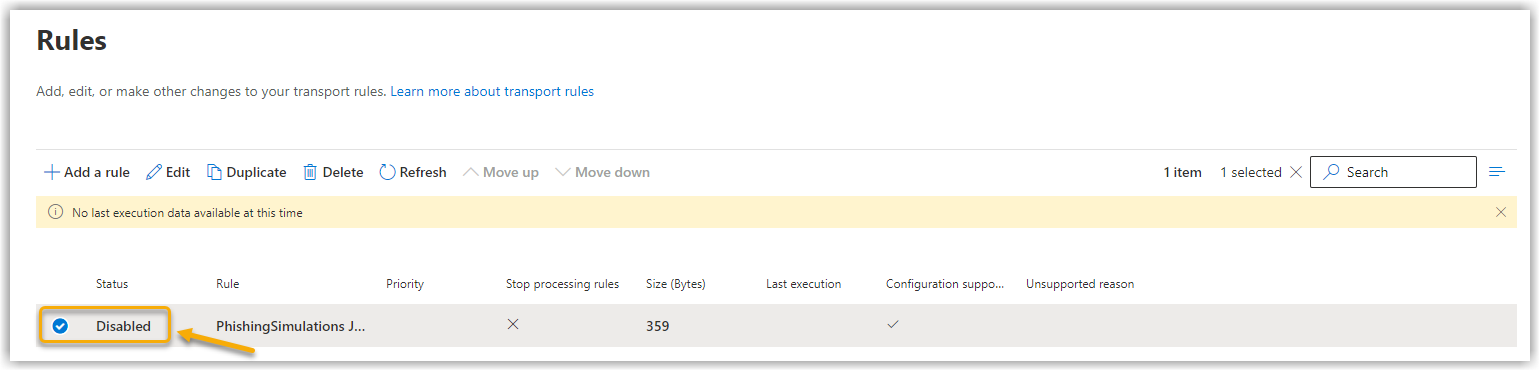
|
||
15. |
Drag the status slider to Activated. Show screenshot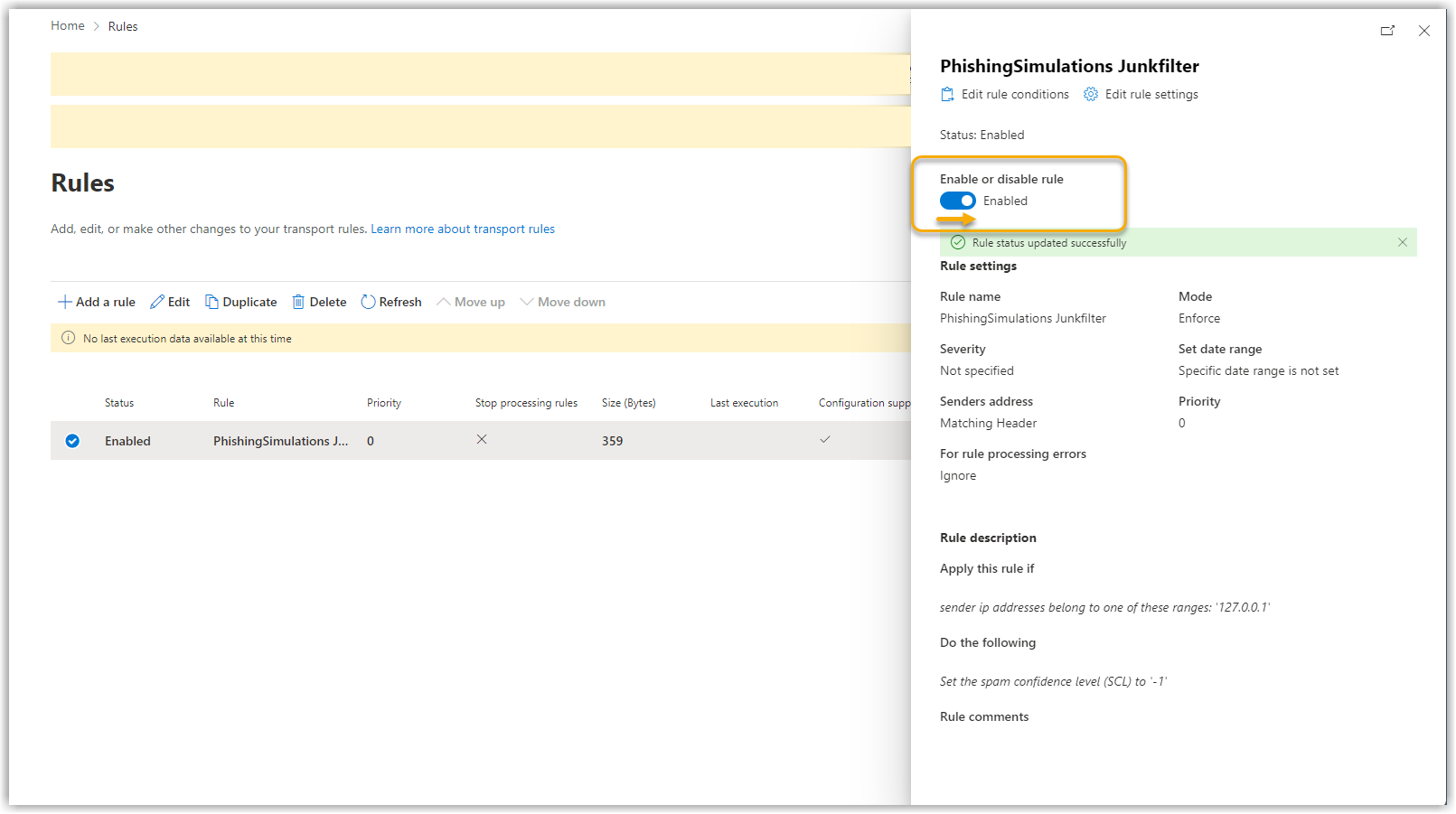
|
||
16. |
Repeat steps 5-15 with the following modifications:
|
The bypass for links and attachments is then set up.