G DATA Phishing Simulation
The G DATA Awareness Manager
With the help of our online platform - the G DATA Awareness Manager - you can send us the information you need about your phishing simulation campaign quickly and conveniently.
In the G DATA Awareness Manager the following information must be stored:
-
the planned participants in the campaign
-
the e-mail address to which the closing reports are to be sent
-
the desired start date
In addition, the G DATA Awareness Manager ensures that a campaign can only be started when the whitelisting was performed correctly.
Edit the following areas in the order you want (except the area Release campaign, as this is where the campaign is started).
Set campaign target
Select whether your participants should receive feedback when they click on our links.
Are your employees receiving phishing emails that have found their way into their mailbox despite all the security measures? Is your IT department informed so that it can take measures to block these emails in future?
And: despite all caution, it can happen to anyone at some point to click on a phishing link. Often such mistakes happen in hectic everyday life. You usually quickly realize that you should not have clicked on this link. It is often just an unpleasant feeling that something is wrong with this link. If the employee quickly reaches out to IT, the damage can frequently still be prevented (for example, by swiftly changing passwords). However, if this oversight is concealed, the attacker has achieved his goal.
Do your employees report to IT after such an oversight has occurred?
This internal reporting process is a key factor in assessing your own IT security.
If the internal reporting process is the focus of your planned G DATA Phishing Simulation, participants should not receive any feedback. In comparison between the "Total number of clicked links in your simulation campaign" and the "Total number of reports of accidental clicks to your IT", you can see how well the participants' sense of responsibility with regard to IT security in your company is.
These findings will help you to assess whether training your employees in the correct handling of data leaks is a priority.
In this case, select Without feedback pages.
A good knowledge of phishing emails and how to recognize them helps to avoid such mistakes in advance. Even under stress, there are criteria that can be used to quickly identify a phishing email.
If you would like to raise your participants' awareness of how to recognize phishing emails, after clicking on one of our links, as well as after entering data on the landing page that opens, a corresponding info page will be displayed for the participant. A campaign can help you to assess whether training on the subject of phishing is necessary for your company or whether the training you have provided has sustainably improved the detection rate of your participants.
In this case, select With feedback pages.
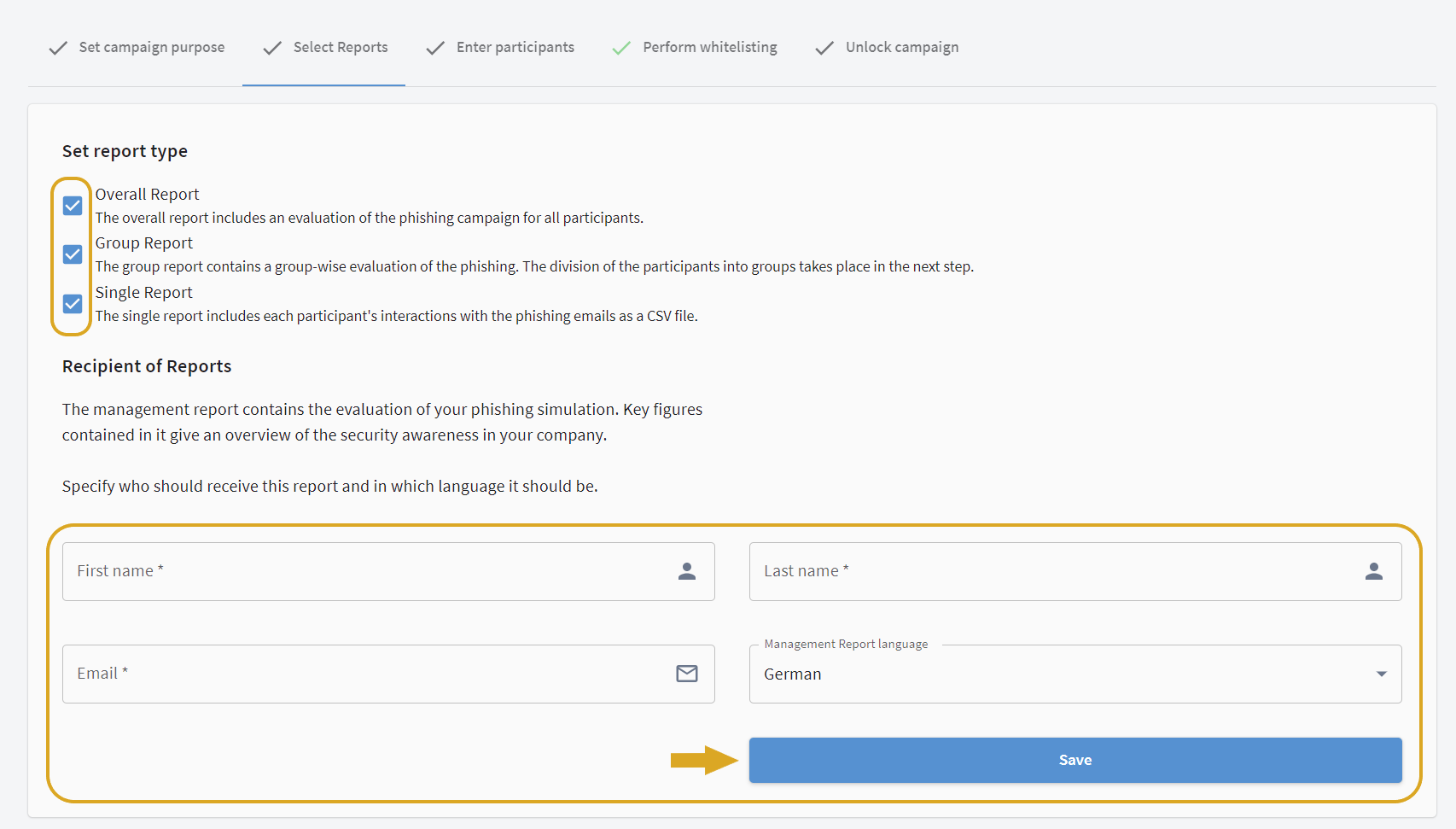
Select reports
Select whether you want
-
an overall report on all participants and/or
-
if you want to receive the included key figures related to specific groups (e.g. grouped by department or by employee/manager).
| Group evaluation is an optional additional service. You can define these groups individually, and it is possible to assign participants to several groups. |
The two options are not mutually exclusive. It is possible to check both boxes. In this case you will receive an overall report and an evaluation based on your groups.
On this page, enter the name of the report recipient, the language in which the reports should be written and the e-mail address of the recipient.
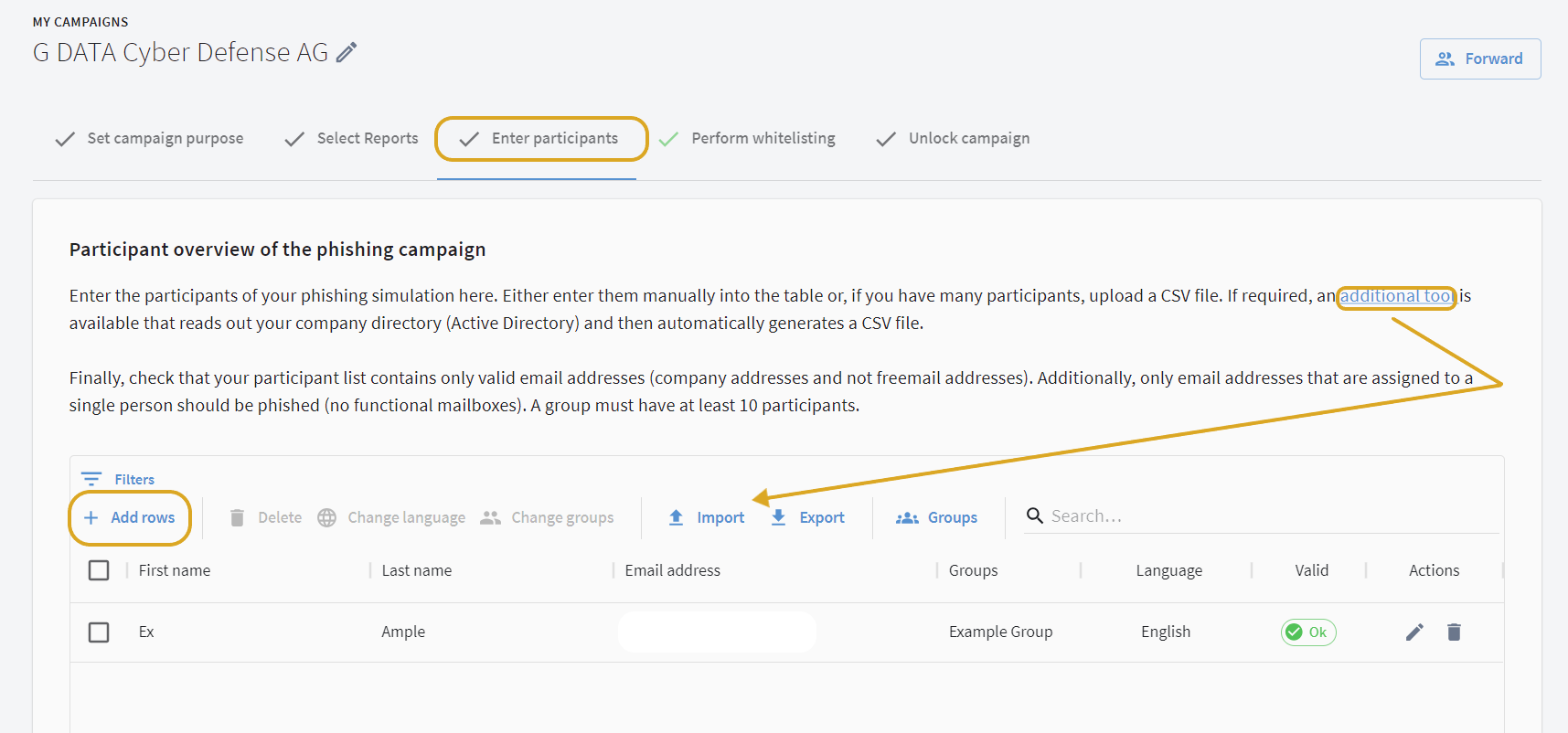
Enter participants
On this page you enter the participants in the G DATA Phishing Simulation. This can be performed by direct input on the page or by import of a previously created CSV file.
Perform whitelisting
Whitelisting depends on the security software you are using. You will find helpful information about it in this article.
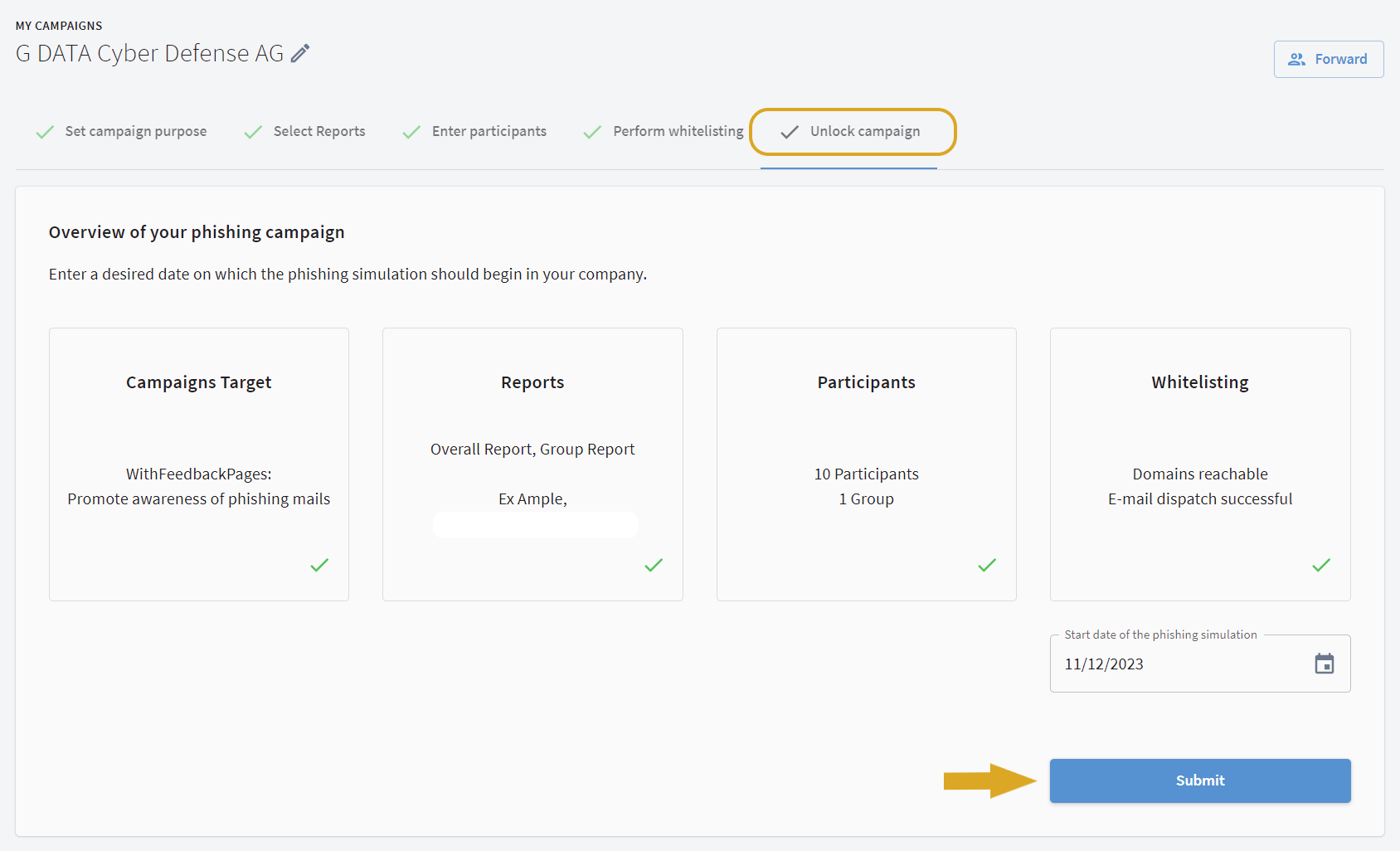
Release campaign
When everything is ready, you will see a view with a green tick for each block. You can now release the campaign.
Involving partners in your phishing campaign
There can be various reasons - from help with the implementation to support with the evaluation - to involve third parties in a phishing campaign.
In the G DATA Awareness Manager you can therefore use the Forward button to invite third parties. These are then given the opportunity to edit the campaign they have been invited to.