G DATA 365 | Managed XDR
Permission management within the roles
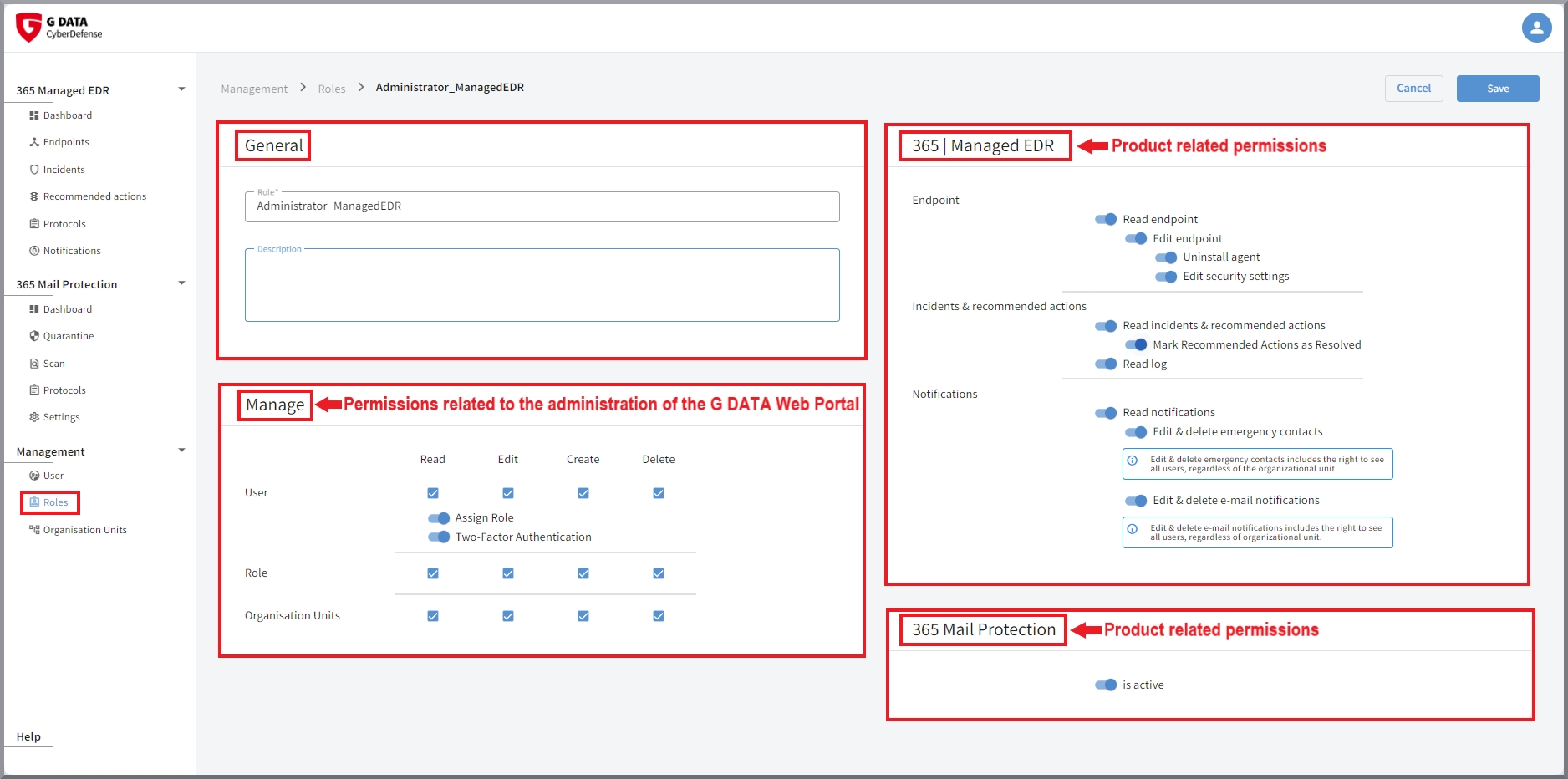
The window is identical for both creating new roles and editing roles. However, the content for customers may differ depending on the license. As various products are managed with the portal, the content depends on the products purchased.
General settings
First of all, there is always a block containing the name of the role and optional notes.
A second block, which is always present, refers to all authorizations required to use the G DATA Web Portal. This determines whether
this role manage users, roles and/or organization units, and to what extent (read, edit, create and/or delete).
2-factor authentication can also be activated in this block, as well as if notifications on the endpoints are displayed in case
any findings occur there.
The corresponding authorization is granted by setting the respective checkmark or toggle switch.
| Only give users with full rights to all products the right to assign roles. Otherwise, a user with limited permissions could set up all other rights themselves without authorization. For example, if users are allowed to manage the portal, but not to see endpoints or mark recommended actions as completed, these users must not have the permissions to assign themselves the missing authorizations. |
| If you cannot see these blocks or if the functions described in this documentation cannot be executed, the logged-in user may not have the required permissions. |
Product related settings
Depending on the product, one or more additional product blocks are also available.
Permissions G DATA 365 | Managed XDR
Here you can set the permissions for the role in regarding the configuration of G DATA 365 | Managed XDR.
Endpoint administration
Read and edit |
Here you define whether holders of this role can see and/or edit endpoints. |
||
Agent configuration |
Deleting endpoints from the portal is linked to the permission to uninstall agents on the endpoints. When starting the uninstallation of the agent, you can decide whether you want to remove the endpoint from the portal at the same time. Persons with permission to uninstall can remove the endpoint from the G DATA Web Portal at a later date.
|
||
Edit security settings |
This permission controls the setting of the agent on the endpoint. This includes the question, whether, in the event of a security event, the reported process should be stopped immediately and whether processing/access should be carried out by G DATA Security Analysts on the affected endpoint. At product launch, a precise list was drawn up with our G DATA Security Operations Team before onboarding as to which of your systems we exclude from the agent’s response or from analysis by our G DATA Security Analysts. This was done after a precise risk analysis. If you have any change requests for individual endpoints during operation, please contact our G DATA Security Operations Team. For security reasons, the IT Operations Manager also does not have the option of changing this setting. |
||
Pause agent |
Here you can configure whether role holders have the option to pause the agent on endpoints for 15 minutes.
|
||
Activate tray icon |
Here you can configure whether role holders have the option of displaying the tray icon of the agent on endpoints. |
Incidents & recommended actions
Read Incidents & recommended actions |
Here you define whether holders of this role can see incidents & recommended actions. |
Mark recommended actions as Resolved |
Here you define whether holders of this role can mark recommended actions as resolved. Option is only available if the role is allowed to see recommended actions. |
Read log |
Here you define whether holders of this role may see the view Protocols. |
Notifications
Read notifications |
Toggle to set whether the specific role receives notifications. |
||
Edit & delete emergency notifications |
Here you can set whether holders of the role can add and remove users from the list of emergency contacts.
|
||
Edit & delete e-mail notifications |
Here you can set whether holders of the role can add and remove users from the list of e-mail notification recipients. In addition, the language of the e-mail and the type of notification events can be set.
|
Permissions configuration G DATA 365 | Mail Protection
If you are using G DATA 365 | Mail Protection, you can specify here whether the product can be configured by holders of this role.
Permissions configuration G DATA Policy Control
If you use the product G DATA Policy Control, you can at this point define which adjustments holders of the role can make in the product.
Device Logging |
Toggle to set whether the role holders can read the device logging. |
Exceptions |
Configuration options for setting whether role holders can read, edit or delete exceptions. |
Global Access Rights |
Configuration options for setting whether role holders can see and/or edit the global access rules, as well as whether they can edit the notifications displayed on the endpoints. |
Permissions configuration G DATA Mobile Device Management
If you use G DATA Mobile Device Management, you can define here whether the product is displayed in the G DATA Web Portal to the holder of this role.